ANON
Hardware wallet user, 2024


We secure keys with world-class encryption and decryption, so your customers can store digital assets with confidence – without ever revealing their keys.

Founded in 2018, we’re the longest-standing provider in the market.
Trusted by over 600 organisations worldwide, from crypto and TradFi institutions, to infrastructure partners and governments.
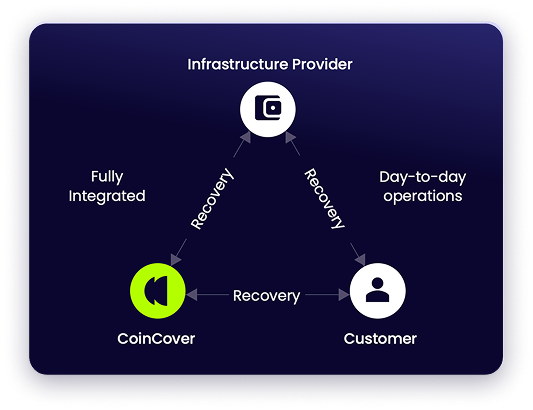
Our breadth of integration with the industry's leading infrastructure providers, and coverage of coins and currencies, is unrivaled.

ANON
Hardware wallet user, 2024
Recover crypto wallets with identity, not memory.
Recover crypto wallets with identity, not memory.
Generate, shard, and secure crypto key material automatically.
Generate, shard, and secure crypto key material automatically.
Create keys securely, without exposing them.
Create keys securely, without exposing them.
Protect crypto keys with multiple layers of encryption.
Protect crypto keys with multiple layers of encryption.


And cool-headed human support when customers need it most.
Explore a practical framework combining 24/7 protection, structured escalation triggers, and automated failovers, designed for institutions that can’t afford downtime.

Talk to us at hello@coincover.com.
Or fill the form.